Protocol isolation, also known as protocol translation, is the practice of confining the use of certain protocols to a specific network location, such as a virtual machine, and isolating it from the rest of the network. As with network segmentation and other types of isolation, such as isolating browsers, protocol isolation helps protect systems against compromises and breaches by keeping all activity local and preventing malware from spreading. It also keeps threat actors from moving through the network.
Protocol isolation is particularly interesting to industrial and manufacturing enterprises, where operational technology (OT) employs a wide range of protocols. This mix of custom protocols involving products of varying complexity and functionality complicates the task of securing an environment. When it’s not possible for teams to individually secure the full range of products and protocols in use, isolating them within their specific areas is the practical approach.
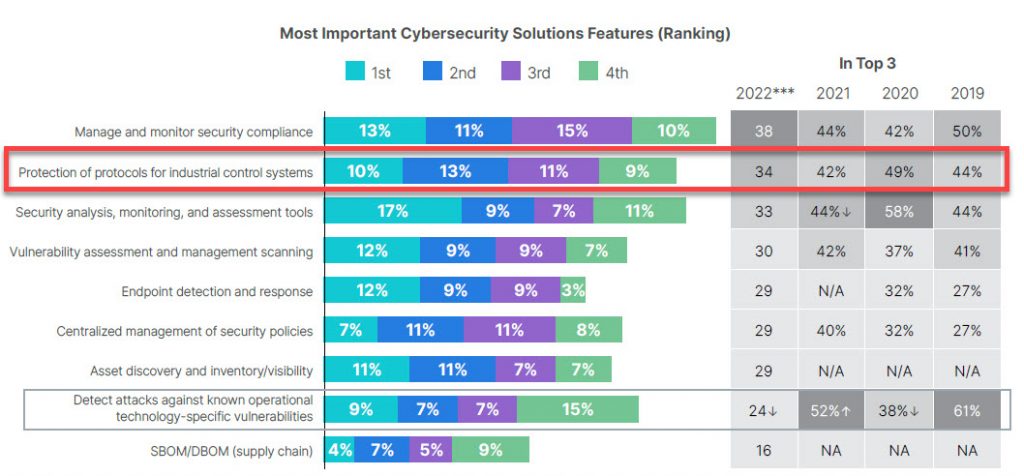
Fortinet’s 2022 State of OT and Cybersecurity Report underscores the importance of protecting protocols for industrial control systems (ICS), which OT professionals ranked as the 2nd most important feature for a cybersecurity solution.
Why Protocol Isolation is Important
Enterprise IT has largely standardized on TCP/IP for most traffic, but within the network several administrative or management protocols are in use, including Simple Network Management Protocol (SNMP), Network Time Protocol, Secure Shell, FTP and Remote Desktop Protocol (RDP).
Organizations that use legacy, unencrypted protocols open the door for malicious actors to harvest credentials and move throughout the network. As the Cybersecurity and Infrastructure Security Agency (CISA) points out, whoever controls the routing infrastructure of a network essentially controls the flow of data. An attacker with a presence on an organization’s gateway router, or internal routing and switching infrastructure, can monitor, modify or deny traffic either to and from the organization or within its network. Isolating protocols and functions, along with segmenting the network, limit what threat actors can do once inside the network.
In industrial settings, the need for protocol isolation is more urgent. Traditionally, OT systems were assumed to be secure because they were isolated from the internet and other enterprise systems. OT systems were “air gapped” from IT systems by being physically separated. Although this didn’t render cyberattacks impossible—malware could be introduced via a USB drive, for instance, as happened in the Stuxnet attack. Even so, it made attacking OT systems difficult and time-consuming, which made compromising those systems less likely than with attacks against IT systems.
In the years since, however, IT and OT systems have converged, combining the use of IT and ICS protocols. That convergence has increased efficiencies, allowing the use of data and analytics to streamline operations, and enabled remote plant operations for geographically dispersed enterprises. But it also has increased vulnerabilities and made OT systems, many of which were never intended to be connected to the internet, a more attractive target for threat actors.
IT systems have standardized on TCP/IP, but OT systems use a wide array of protocols, many of which can be specific to the functional operations of equipment, the type of industry or even geographical areas. Integrated IT and OT systems may use the same hardware, but they still operate differently, with significant differences in the software and protocols used.
In addition to the variety of OT protocols in use, many OT systems are also older, with more than half running unsupported and unpatched software. Many rely on outdated operating systems, with Windows XP still in widespread use. OT systems that are run networked with IT systems can also be vulnerable through open ports that lack proper access and protocol controls.
These factors have increased the importance of protocol isolation. The air gaps that once existed between OT and IT systems have to be effectively replicated by other means in order to protect those systems. Protocol isolation is one way to do that.
How Isolating Protocols Improves Network Security
The practice of isolating systems, protocols and other elements of a network is gaining attention as enterprises become increasingly cloud-based and dispersed. Treating OT like an enterprise network will lead to disaster because its systems and requirements are entirely different. While an enterprise network can withstand a data breach from unauthorized network access, gaining access to a nuclear power plant’s control systems is of a different magnitude and requires protocol isolation, which offers higher level of security controls.
Network segmentation, also known as network isolation, is one way to prevent threat actors who have gained access to a network from moving around within the network to steal data or inflict damage. A network is divided into sub-networks, or zones, of systems that share operational functions and risk profiles. Communication between the subnets, which consist of Virtual LANs, is prohibited unless specifically granted.
Segmentation is often a crucial element of Zero Trust security strategies. Network segmentation also allows for the isolation of assets within the network, managed by a firewall that can enforce access controls and security policies. A firewall configured for OT-specific protocols, for instance, can inspect traffic for potentially malicious content or activity.
The goal of isolating protocols is to help stop threat actors or malware from lateral movement within the network, a tactic that commonly used tools aren’t equipped to prevent. Outdated VPNs, for example, weren’t designed to manage access to critical systems, and do not isolate systems or protocols. An attacker who uses stolen credentials to access a network via a VPN could have free movement once inside.
Along with other security measures such as enforcing the principles of least privilege and securing access to devices within the infrastructure, organizations can use protocol isolation and segmentation to restrict movement. Some recommended best practices include:
- Logically segregate the network by physical or virtual means, which allows admins to isolate critical devices and their protocols within network segments. Virtual LANs (VLANs) are the most common way to segment networks.
- Use protocol-aware firewalls configured to filter traffic and deny the flow of packets within the network.
- Implement a VLAN access control list, which filters access to and from VLANs, based on protocols, ports and the direction of traffic, denying the flow of data from one VLAN to another.
Protocol isolation is a part of a comprehensive, holistic approach to security. One of the tenets of modern security strategies such as Zero Trust is to operate on the assumption that the network has already been hacked. Protocol isolation mitigates the damage from those successful attacks, potentially stopping them before they can do damage while also limiting the movement of attackers inside the network.
How XONA Uses Protocol Isolation
XONA enables frictionless user access that’s purpose-built for operational technology (OT) and other critical infrastructure systems. Technology agnostic and configured in minutes, XONA’s proprietary protocol isolation and Zero Trust architecture immediately eliminates common attack vectors, while giving authorized users seamless and secure control of operational technology from any location or device. XONA’s proprietary protocol isolation allows organizations to securely stream applications and convert remoting protocols into an encrypted display that can be presented into any browser. With integrated multi-factor authentication, user-to-asset access controls, user session analytics, and automatic video recording, XONA is the single, secure portal that connects the cyber-physical world and enables critical operations to happen from anywhere with total confidence and trust.
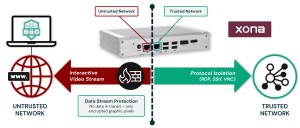
Protocol isolation allows protocols to be accessible on a trusted ICS network but closed to external untrusted networks and users unless they are using a solution that translates the protocols from the trusted network to the untrusted network without exposing the native protocols. XONA’s secure user access platform is just one example of this solution. Secure user access platforms securely stream applications and convert remote protocols into an encrypted display presented in any browser. This is a fundamental shift in thinking and breaking the kill chain before network access begins. As a result, protocols that hackers could exploit traditionally are now closed due to protocol isolation which dramatically reduces the attack surface of the OT and ICS networks. Protocol isolation removes the need for Jump Servers, VPNs, and other related IT/OT and cybersecurity technologies and network gear.
Below is a visual depicting XONA’s approach to protocol isolation in our CSG gateway, which does the translation but only sends out PNG images over port 443. In this example, RDP or VNC protocols are not accessible from the internet or external networks, eliminating the attack surface.
Learn More
- XONA CSG Capabilities Datasheet
- ISA/IEC 62443 Cybersecurity Standards Datasheet
- How to Securely Transition to Remote Plant Operations in Response to Today’s Challenges
- US Officials Warn – Heightened Risk of Ransomware Attacks on Municipal Utilities
- The Case for Zero Trust Access for the Industrial Internet of Things
