The demand for technology that can support secure user access, both remote and onsite, has expanded beyond IT environments to include the operational technology (OT) and industrial control systems (ICS) that enable organizations in a variety of critical infrastructure (CI) sectors to function.
However, the priorities of IT environments (i.e., the confidentiality, integrity, and availability of data[1]) are inherently different than those of OT environments (i.e., the safety, reliability, and availability of operations[2]). The latter holds the potential to bring significant harm to humans and the environment if the environment were controlled by someone with malicious intent.
In addition, it is not unusual in critical infrastructure environments for OT/ICS assets of varying complexity, functionality, and states of cybersecurity to be connected using a mix of network protocols. This can complicate the task of securing a trusted OT network from cyberattacks. As such, when it’s not possible for teams to individually secure the full combination of assets and protocols in use, isolating them individually within their specific network is a smart approach.
In fact, in Fortinet’s 2022 State of OT and Cybersecurity Report OT professionals ranked the “protection of protocols for industrial control systems” as the second most important feature for cybersecurity solutions.
Why Protocol Isolation is Important
Enterprise IT has standardized to a great extent on the Transmission Control and Internet Protocols (i.e., TCP/IP). However, as stated previously, within an OT network environment, several protocols are often in use. These may include the Remote Desktop Protocol (RDP), Secure Shell Protocol (SSH), Virtual Network Computing (VNC) protocol, and others.
Organizations that use these protocols may open the door for malicious actors to harvest credentials and move throughout the network. As the Cybersecurity and Infrastructure Security Agency (CISA) points out, whoever controls the routing infrastructure of a network essentially controls the flow of data. An attacker with a presence on an organization’s gateway router, or internal routing and switching infrastructure, can monitor, modify, or deny traffic either to and from the organization or within its network. Isolating protocols and functions, along with segmenting the network, limits what threat actors can do once inside the network.
In industrial settings, the ability to isolate protocols such as RDP, SSH, and VNC is critical. Traditionally, these protocols were assumed to be secure because they were used in OT environments with assets that were “air gapped” from the public Internet and IT networks. This made attacking OT environments difficult – if not impossible and made attempts to compromise them less likely than attacks against more “target rich” IT systems.
However, IT and OT systems are converging, combining the use of both IT and OT protocols. That merging has increased efficiencies, allowing the use of data and analytics to streamline operations, and enabled remote plant operations for geographically dispersed organizations. But it has also introduced vulnerabilities and made OT systems, many of which were never intended to be connected to untrusted networks, a more attractive target for threat actors.
So, while IT has standardized on TCP/IP, the world of OT/ICS still uses an array of protocols, many of which can be specific to the functional operations of equipment, a type of industry, or even geographical locations. Integrated IT and OT systems may use the same hardware, but they still operate differently, with significant variations in the software and protocols used.
Too many OT systems are also outdated from a systems standpoint, with them running unsupported and/or unpatched software. These systems may rely on outdated operating systems, such as Windows XP. OT systems that are networked with IT systems can also be vulnerable through open ports that lack proper access and protocol controls.
Each of these factors has increased the importance of protocol isolation, as the air gaps that once existed between OT and IT systems need to be effectively replicated by other means to protect those systems.
How Isolating Protocols Improves Network Security
The practice of isolating systems, protocols and other elements of a network is gaining attention as organizations become increasingly cloud-based and geographically dispersed. Treating an OT network like an IT network holds the potential for disaster given very different priorities. While an IT organization may recover from a data breach by a malicious actor, someone gaining access to a nuclear power plant’s control systems speaks to the potential for a far more dire set of consequences.
Network segmentation is one way to prevent malicious actors who may gain illegal access to a network from moving laterally across the overall network to steal data or inflict damage. However, network segmentation can be very complex and invasive – and CI organizations often don’t have the networking expertise for such an initiative.
The goal of protocol isolation is conceptually like network segmentation, except it is the network protocol and the assets to which they are connected that are isolated. And unlike network segmentation, it does not need to be either complex or invasive.
Protocol isolation can prevent malicious actors from lateral movement across a network. It can also address one of the shortcomings of the VPN technology used by some CI organizations, which aren’t designed to isolate protocols or prevent lateral movement within a network. This is especially true if done in concert with a zero-trust architecture that enforces the principles of least privilege.
How XONA Uses Protocol Isolation
As mentioned previously, the demand for technology that can effectively support secure user access, both remote and onsite, has expanded to include the OT and ICS that enable organizations in a variety of critical infrastructure (CI) sectors to function.
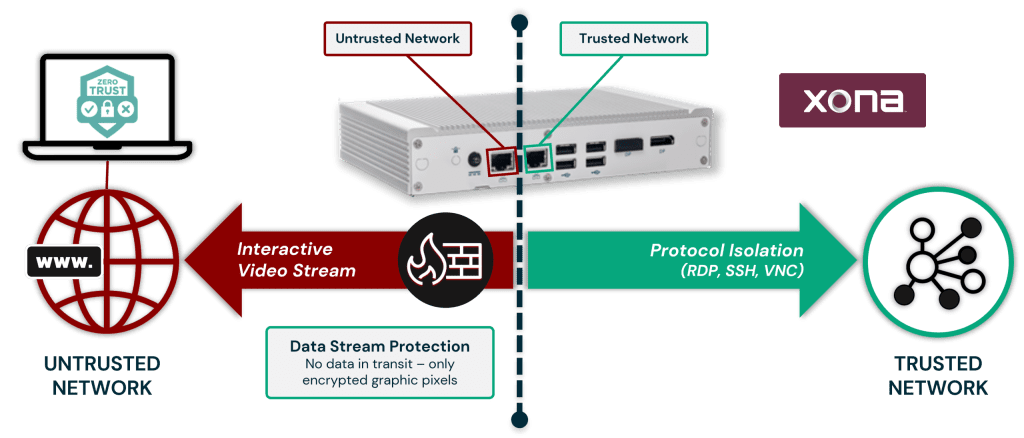
Given security concerns about allowing access by bad actors into these environments, the XONA Critical System Gateway (CSG) is delivered with protocol isolation as a core piece of its feature set. It confines the use of RDP, SSH, and VNC protocols to a specific trusted network and isolates them from untrusted environments, such as the Internet or an IT network.
In addition, once a live data stream from an OT/ICS asset reaches a XONA CSG it is converted into graphics files and presented (bi-directionally) to the OT/ICS operator as an encrypted interactive video stream. This eliminates the possibility of a bad actor inserting malicious commands into the conversation between an OT/ICS operator and the XONA CSG.
Below is a visual depicting XONA’s approach to protocol isolation in our CSG gateway.
Learn More
- XONA CSG Capabilities Datasheet
- ISA/IEC 62443 Cybersecurity Standards Datasheet
- SANS Report: The State of OT/ICS Cybersecurity in 2022 and Beyond
- US Officials Warn – Heightened Risk of Ransomware Attacks on Municipal Utilities
- The Case for Zero Trust Access for the Industrial Internet of Things
References:
